Research
Research
FACES: Tokyo Tech Researchers, Issue 44

Issue 44
Hideaki Ishii
Department of Computer Science, School of Computing
With the advance of technologies such as autonomous driving and smart grids, increasing importance is being placed on cyber-physical systems that use information and communication technology (ICT) in cyberspace to optimally control devices in physical space. Amidst these developments, Professor Hideaki Ishii (Department of Computer Science, School of Computing) is leading the field in research on control theory related to cyber-physical systems.
Every day, people throughout the world connect using smartphones and personal computers. We are always in contact with new information, and we disseminate information ourselves via emails and social media. On the other hand, human beings are not the only things closely connected by ICT. Today, many devices such as home appliances and automobiles communicate via networks and are controlled from moment to moment.

For example, today's automobiles are equipped with about 70 electronic control units. These units control everything from engines and brakes to air conditioning through the in-vehicle network. Moving forward, as autonomous driving advances, communication will expand beyond in-vehicle equipment to include external networks. For example, there will be communication among vehicles and various sensors installed in urban environments. This will enable even more advanced control.
Control is also fulfilling an increasingly important role in the energy field. Currently, the introduction of smart grids is being promoted to prevent global warming. A smart grid is a power grid that uses ICT to efficiently distribute power by automatically controlling power supply and demand in real time. This is expected to promote the optimization of power generation facilities and the introduction of renewable energy.
A system that uses ICT in the cyberspace to control devices in the physical space is called a "cyber-physical system" (CPS). By linking devices and ICT and feeding back the results of data analysis in the cyberspace to devices, it is possible to achieve even more optimal control of devices in response to changes in the environment. CPSs are gaining importance not only in autonomous driving and smart grids, but also in various fields such as disaster response by robots and aerial transportation by drones.
Professor Hideaki Ishii (School of Computing) has been focusing on CPSs from an early stage and researching the related control theory. Ishii was one of the first researchers to realize the essential issues in fusing control theory and ICT, and his achievements in researching theory for that purpose have been highly regarded. In 2021, Ishii was awarded the title of Fellow by the Institute of Electrical and Electronics Engineers (IEEE), which is the world’s most distinguished organization in the fields of electrical, electronics, and computer engineering.
Based on control engineering, Ishii is currently conducting theoretical research on CPSs in three directions: (1) communication constraints, (2) large-scale multi-agent systems, and (3) security and learning (Figure 1). Each direction of research is introduced in detail below.
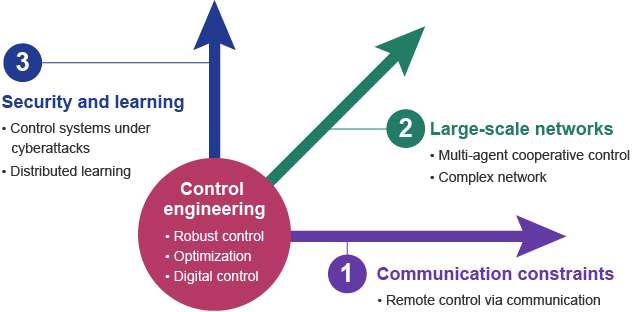
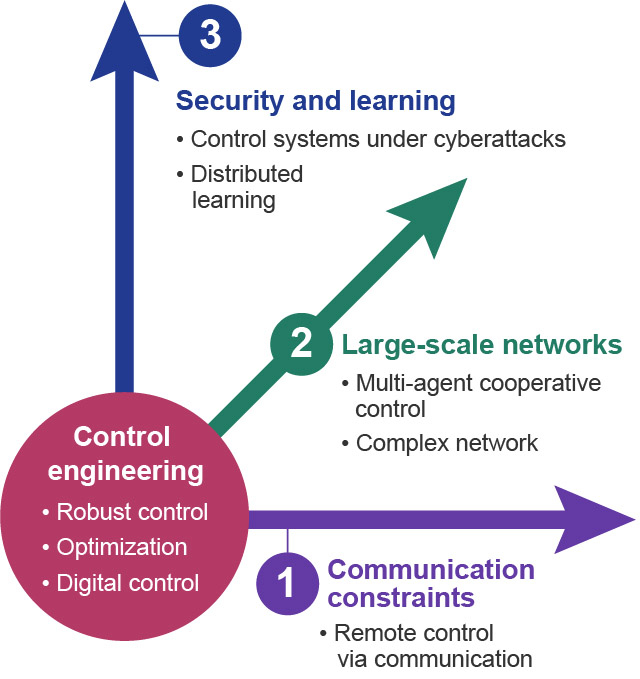
Figure 1. Three axes of theoretical research on CPS
First we discuss (1) communication constraints.
"Networks have been installed in automobiles and factories since the 1990s," says Ishii when explaining the history of control through networks. "Transmission delay is just a minor annoyance when browsing the internet on a smartphone or personal computer; however, transmission delay is a serious problem when controlling an engine or brakes. Even a delay of just 0.5 seconds between braking and stopping can lead to a serious accident. Furthermore, when multiple systems share a single communication network, it is extremely important to determine which system should be given priority for use."
As explained by Ishii, communication networks used for control have their own unique constraints. "In the 1990s, no one was examining the theoretical issues in these systems," explains Ishii. "Professor Roger Brockett of Harvard University first raised this issue around 2000. At the time, I was a doctoral student in the Department of Electrical and Computer Engineering at the University of Toronto, Canada. I recognized the new possibilities that communication networks bring to control engineering, and decided to make it the theme of my doctoral dissertation. This was a major turning point for my research. Until this day, I have been conducting research to link control theory with the theory of information and communication. In 1948, the American mathematician Norbert Wiener (1894 to 1964) proposed the fusion of control and communication technology in his influential book Cybernetics. However, it is interesting that the past 20 years are the first time that systematic theoretical research has truly been performed."

Ishii cites the "inverted pendulum" as an example to explain the fundamentals of using networked control to stabilize an ever-changing, unstable system that is under communication constraints.
In this system, a rod that can be tilted in any direction by 360 degrees is placed on a dolly. A motor is used to move the dolly and control is performed to prevent the rod from falling over. A sensor is used to measure the angle between the dolly and the rod in real time, and the posture of the rod is controlled based on that angle. Instead of imagining a dolly, this example is easier to understand if you imagine a long, thin stick standing on the palm of your hand. You can prevent the stick from falling over by moving your hand back and forth.
"Suppose that we use a communication network to connect a sensor that measures the angle of the rod and a controller that determines the movement of the dolly," explains Ishii. "At this time, in order to reduce the amount of communication used for control, we must reduce the amount of measurement data sent from the sensor as much as possible. It is important to clarify the extent to which the amount of data can be reduced."
In response, Ishii devised a method called quantized control. The rod can fall in any direction of 360 degrees. However, these directions can be divided into segments. For example, 360 degrees can be divided into 12 segments of 30 degrees each, and the sensor can measure which segment the rod is in. Quantized control is such a process of converting physical quantities that take continuous values into discrete values for control. This makes it possible to significantly reduce the amount of information. As an extreme case, it is conceivable to reduce the number of segments to two. However, if the only information available is that the rod has tilted to the right or left from an upright position, the rod will quickly fall over. Therefore, it is necessary to perform control while predicting the movements of the system using a mathematical formula that serves as its physical model.
"In an unstable system, the degree of instability is represented by a value called the 'unstable pole,'" explains Ishii. "In an inverted pendulum, the mass and length of the rod determine the unstable pole. Assuming that rods have the same mass, the longer the rod, the greater the stability. One interesting fact is that the theoretical minimum required speed for the communication network is determined solely by the value of the unstable pole."
Next, let us move on to (2) large-scale multi-agent systems.
When discussing (1) communication constraints, we introduced an example related to automobile control. This example referred to the control of a single vehicle. However, as autonomous driving progresses in the future, control will advance through communication networks among vehicles and with various sensors in the urban environment. This is the research on (2) large-scale multi-agent systems.
"Multi-agent" means that there are many agents and each agent makes decisions autonomously; however, the system as a whole aims to behave in a specific way.
Multi-agent research targets are wide-ranging. Active research is being conducted for applications such as autonomous driving of automobiles, flight control of drones, and sensor networks using wireless communication. Furthermore, through these mathematical models, it is possible to use multi-agents to examine phenomena such as how COVID-19 spreads, how people's opinions spread on social media, and how cranial nerves synchronize in our brains. Ishii reconsidered multi-agents from the viewpoint of control theory and is researching their control methods.

Sensor networks

Drone formation flight
Smart grids

Autonomous driving
As his underlying idea, Ishii cites the collective behavior of flocks of birds and fish as an example.
There is no leader in the group. Each autonomous individual changes direction and speed at its own will. However, let's assume that there is an intention to gather together as a group and move in a certain direction. Individuals can only see their close companions.
According to Ishii, the most important point in such multi-agent systems is the communication of information among agents. Figure 2 shows a method of mathematical expression known as a "graph." In this graph, the numbered circles represent agents. The arrows connecting numbered circles represent the connection between agents, i.e., the transmission of information.
"In Figure 2, there are eight agents who exchange information with a limited number of fellow agents and update the direction of their own behavior," explains Ishii. "Matching directions means that the angle difference between your own direction and the other agent's direction is 0. This state is known as a 'consensus' in the field of algorithms. The ‘consensus problem’ is a very important problem when considering multi-agents."
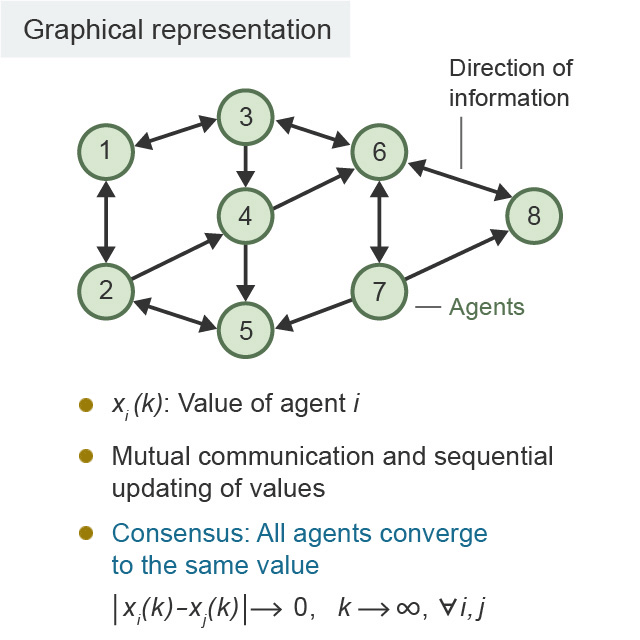
Figure 2. Network of agents
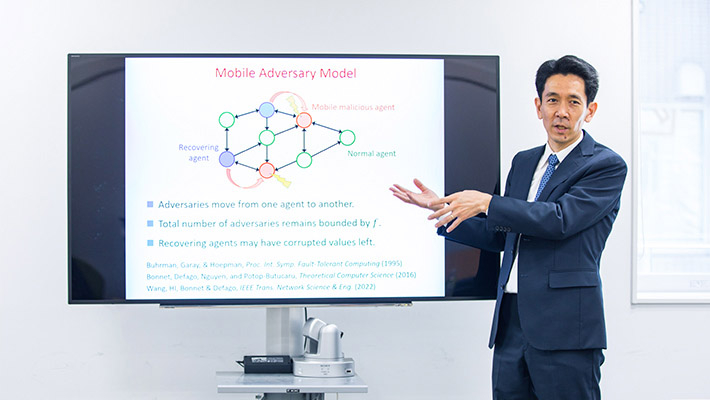
In particular, there has recently been extensive research on consensus algorithms for cases in which a system contains agents that behave abnormally (Figure 3). "Suppose you have a selfish agent in your group who doesn't care about the other members," says Ishii. "Even if all members agree, a system will not be reliable if it is impacted by such a selfish agent. When certain agents behave significantly differently from others, the system works well by 'ignoring' such agents. On the other hand, this raises the new problem of how many agents that behave abnormally can be tolerated."
Here, the important point is that the denser the connections between agents in the system, the more abnormal agents that can be tolerated. This is also a problem for distributed algorithms in the computer science field. Ishii’s research clarified the minimum connection conditions that a network should satisfy.
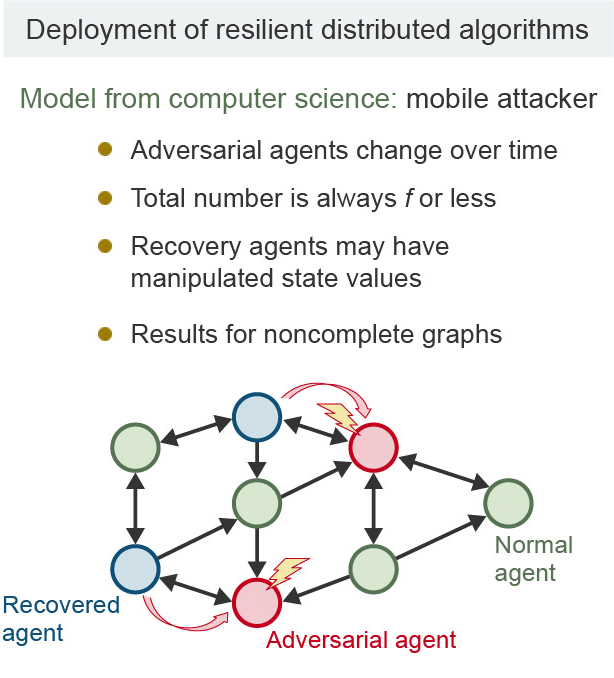
Figure 3. Consensus in a multi-agent system including anomalous agents
Such research is directly linked to safe operation of autonomous distributed control. "I am also working on distributed control for smart grids in the energy field," says Ishii. "Moving forward, I believe that an increasing amount of research will be conducted on autonomous distributed control that is resistant to failures and abnormalities."
Ishii is in fact involved in research on security in large-scale cyber-physical systems. This is the last direction (3) security and learning.
In the case of control via a communication network, there is the risk that someone with malicious intent will tamper with information, thereby causing control to be performed differently than expected. Therefore, Ishii is researching security from the perspective of control theory to determine to which extent a system can withstand attacks.
In a large-scale cyber-physical system like the one shown in Figure 4, there is a physical network in the physical space and a control communication network in the cyberspace. These two networks are linked to each other through local monitoring and control.
"For example, jamming of communications and falsification of control information are assumed as attacks on communication networks," describes Ishii. "The scary thing about such attacks is that they can change control command signals and manipulate devices in the physical space to behave abnormally. I am currently conducting theoretical research on methods for detecting attacks from both the physical space and the cyberspace."
This research has created new perspectives that did not exist in the past in control theory. This is because this line of work also examines the perspective of the attacker and considers the completely opposite problem of implementing control in the worst possible way for the system. Of course, based on such research, Ishii’s job is to propose methods for constructing safer systems. He is also conducting research to improve performance by having AI learn the communication patterns of cyberattacks.
"In this way, as large-scale cyber-physical systems continue to spread, I feel that theoretical research in fields fusing control and information/communication is rapidly increasing in importance," says Ishii.
Distributed system mechanism for cyberattack detection and robust control
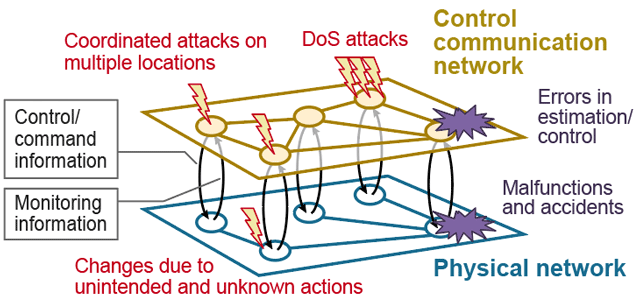
Figure 4. Cyber-physical security
What spurred Ishii's desire to study control theory?
"As a child, I had the opportunity to live overseas," explains Ishii. "Upon returning to Japan, I had a vague wish to work internationally in the future. I became interested in theoretical research when I was wondering what path to choose during my sophomore year at the University of Tsukuba. In particular, I was fascinated by the story of how a prominent engineer named Rudolf Kalman (1930 to 2016) laid the foundations of control theory almost all by himself in the 1960s. The story inspired me to pursue this field. I also liked that it is fundamental to different branches of engineering such as mechanical, electrical, aerospace, and so on."

Afterward, Ishii entered the Master's program at Kyoto University. Following his studies there, he went on to the doctoral program at the University of Toronto. After working as a postdoctoral associate at the University of Illinois in the United States, he entered the Tokyo Institute of Technology in 2007. "Currently, I really enjoy engaging in interdisciplinary joint research with colleagues from all over the world," says Ishii. "That is the real thrill of research."
In closing, Ishii gave the following message to young people who want to become researchers. "In order to establish a career as a researcher, it is important to think deeply and continue over the long term," explains Ishii. "In addition to finding a field that interests you, it is good to find a research style that suits you. For example, while theoretical research may seem like a solo effort, it is becoming increasingly important to develop new fields through discussions and collaboration with researchers from different fields. International research activities are also essential. For that reason, I strongly recommend studying abroad at an early stage, which should include improving your English skills. I hope that young researchers will be curious and seek to expand their research networks."

Professor Hideaki Ishii
Department of Computer Science, School of Computing
School of Computing
—Creating the Future Information Society—
Information on School of Computing inaugurated in April 2016
The Special Topics component of the Tokyo Tech Website shines a spotlight on recent developments in research and education, achievements of its community members, and special events and news from the Institute.
Past features can be viewed in the Special Topics Gallery.
Published: October 2023